
Mortgage Finance Gazette has partnered with Mortgage Strategy and The Openwork Partnership to bring you MFG Rated for Service 2025.
This is the only broker survey to recognise service in the UK mortgage lending industry. Last year over 600 brokers took the time and trouble to share their experiences with us for which we are truly grateful.
There have been challenges aplenty in the mortgage industry this year, which is more reason to celebrate those who overcame adversity to provide excellent service.
Mortgage brokers are called on to provide invaluable feedback through the survey, acknowledging both achievements and areas that require improvement, to ultimately lead to better client outcomes.
MFG Rated for Service is based on a comprehensive annual survey that tracks brokers’ assessments of the lenders’ levels of service over the last 12 months.
Lenders are appraised across five key assessment areas within three separate peer groups categorised as mainstream, specialist and buy-to-let. Your voice counts and your experiences matter.
To view or complete the survey please click here.
If you are a lender or network, we would strongly encourage you to prompt your broker networks to give us their views to ensure they are represented and we would be happy to provide any marketing assets to you to assist with this.
Please contact indigo.marketing@emap.com for further information and promotional assets.
The survey closes on 9 January 2025 and results will be published in Mortgage Finance Gazette and Mortgage Strategy in March 2025.
Calling all brokers – have your say on lenders’ service levels – Mortgage Strategy
If You’re Serious About Selling Your Home, List Below the Zestimate
Recently, I’ve encountered two very different types of for-sale listings in the market.
There are the properties that go pending in about a week, essentially flying off the shelf.
And there are the listings that fester on the market for months with little to no action.
Often, the difference is simply in the price, not the quality or amenities of the home.
So if you’re serious about selling in today’s housing market, think lower instead of higher.
Choose a Listing Price Below the Zestimate or Redfin Estimate
One of the easiest ways to drum up a lot of excitement for your home is to simply price it right.
This generally entails listing it for a lower price versus a higher price. But what’s low and what’s high?
Well, your real estate agent should be able to help you out on that one, but there are also simple clues to figure this out.
Most properties have an associated Zestimate, which is Zillow’s estimate of a home’s market value.
No, it’s not an actual home appraisal, nor can it be used in lieu of an appraisal, but it’s often a decent starting point to determine value.
The same feature can be found on Redfin and is known as a Redfin Estimate. Same concept, just a different company.
And even Realtor has its so-called “RealEstimate,” which features three different home value estimates.
Sometimes these estimates are higher or lower than the other. For example, your Zestimate might be lower than your Redfin Estimate. Or vice versa.
Anyway, a good agent will look at sales comparables in the immediate area that sold recently when determining a good listing price.
They may also tell you to ignore the Zestimate or Redfin Estimate and that it’s not accurate, blah blah.
But, and this a very important detail, will your prospective buyer look at recent comps or will they look at the Zestimate? Chances are it’ll be the latter.
Why? Because they are consumers and these types of estimates are 100% geared toward consumers, aka home buyers. They are quick and dirty and well-known and easy to wrap one’s head around.
Digging into actual sales comps is a more involved process and one that could go over a buyer’s head.
Let’s Consider an Example
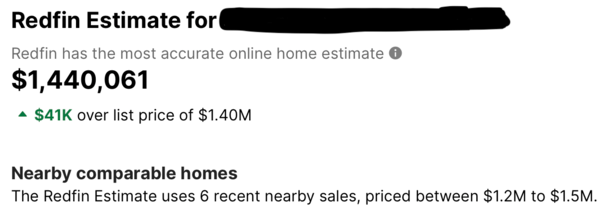
I recently came across a property that was pending in about nine days. That’s pretty darn good, given it’s been very tough year for the housing market.
A combination of high mortgage rates (relative to recent years) and still-rising home prices has put a major strain on affordability.
At the same time, listing in November or December typically isn’t ideal as there will usually be fewer buyers in the market.
After all, they’ll be more focused on year-end stuff, shopping, holidays, traveling, etc. The weather could also play a role.
Despite this, a property in Southern California went from list to pending in nine days.
And if you look at the list price compared to the Zestimate and Redfin Estimate, it was priced just below.
This matters because as prospective buyers peruse listings, they will see these estimates. And it will tell them if the list price is below or above the estimated value.
Human psychology will tell them it’s a deal if it’s priced below the estimate. Just like any other product you buy, it will be perceived to be “on sale” or “discounted.”
No different than a pair of shoes that are 20% off, it’ll feel like you’re getting more for less.
Conversely, if it shows the list price above the estimate, that buyer might be turned off and feel the seller is being greedy.
This could result in the buyer moving on and considering other properties instead.
Also Make Sure the Price Is Below Key Thresholds
Other than listing below the Zestimate, it can also be helpful to list below a key pricing threshold.
For example, if the Zestimate is $1,520,000, going with a list price of $1,499,000 accomplishes two things at once.
You get it below the Zestimate and you get it below $1,500,000, which might be a user’s maximum price in their app settings.
This could open up the property to more users who may have their setting adjusted to only see properties listed for sale under $1,500,000.
If you were to put $1,505,000, which is still below the Zestimate, some users could miss your property, even if it were affordable to them.
Similarly, if the Zestimate is say $520,000, listing at $499,000 could accomplish the same result.
And if you’re worried about the property selling for less due to a lower listing price, that might not actually be the case.
Often, you can garner more interest for your listing if it’s priced lower, and possibly get multiple bids, better terms, etc.
It can actually be riskier to list high, watch the property sit on the market, then be forced to apply a price reduction and wind up in a similar place.
Why Aren’t More People Doing This?
A common gripe from real estate agents is that their client didn’t listen to their advice on setting the listing price.
In other words, the seller wanted to list it for more than the agent. Go figure, right?
From the agent’s point of view, a lower list price doesn’t result in a much smaller commission because they only earn 2-3% of the sales price. So if it’s $50,000 less, their cut might only be about $1,000.
But for the seller, every dollar counts. It’s potentially $50,000 less!
However, it could be even worse if the property sits on the market for months. As for why sellers are listing high, my guess is they’re often would-be sellers.
They will sell, but they don’t have to sell. So they’ll throw the property up on the high end of the price range and wait and see.
Often, this results in a lot of waiting, and eventually seeing that nothing has happened. It’s still listed months later with few to zero bites.
Of course, they might not care all that much since these types of sellers are merely just testing the waters and aren’t all that serious.
Read on: It’s Okay to Negotiate with Your Real Estate Agent
Tips to Gain Financial Empowerment

Feelings of financial security are on the rise in the U.S., with 33% of Americans saying they don’t feel financially comfortable in 2024.
That’s a 6% jump from the previous year. But it’s possible to reverse those feelings to be in a better position and feel confident about your finances.
Here are several ways to move forward and begin your personal journey to financial empowerment.
#1: Set a goal
Empowerment can mean different things to different people. Depending on your financial situation, your priorities will be different from someone else’s. That’s why it’s important to choose your own definition of financial empowerment. And this can be done in stages.
First, think about what would make you feel financially secure at different stages of your life. From there, you can define short-term, mid-term and long-term goals that reflect your vision of financial empowerment.
#2: Make a budget
Whatever your goals may be, the next step is to create a budget. This is an empowering process because it gives you control over how you spend and save each dollar. The initial process is simple:
- Tally up how much cash hits your bank account each month
- Calculate your fixed expenses
- Adjust your variable expenses based on the money left over
- Figure out how much you have left to put towards your goals
Revisit your budget each month to see what changes you want to make. Nothing is set in stone, and you may have different levels of income or expenses at various times.
#3: Build an emergency fund
No matter your overall goals, it’s important to have a solid emergency fund in place. That way, you’re prepared for surprise expenses, like a car repair or hospital visit.
There are many different opinions on how much you should have in this fund, from as little as $500, all the way up to several months’ worth of expenses.
Reflect on the past several years of expenses you’ve had to choose a goal that feels right for you.
#4: Monitor your credit score
Monitoring your credit score is empowering in a couple of different ways. For starters, it helps you prepare to get the best financing rates when you want to borrow money.
If your score is lower than expected, you can see what has caused a drop and what steps you can take to fix it. Improving your credit takes time, so it’s smart to make this an ongoing practice.
The second reason you should monitor your credit score is to check for any identity theft or fraud. You’ll quickly notice if there is any suspicious activity so you can address issues (like a fraudulent credit card opened in your name) before they become too serious.
#5: Target high-interest debt
Paying off high-interest debt can be extremely empowering. 73% of Americans cite debt as a significant source of stress, so reducing or eliminating large balances can help your day-to-day anxiety levels.
Strategically managing your debt can go beyond making minimum payments. Consider options like:
- A debt consolidation loan or a 0% APR credit card to simplify repayment and potentially save on interest
- Paying off the highest interest balances first (known as the debt avalanche method) can reduce total interest costs
- Tackling smaller balances first (the debt snowball method) to build momentum and stay motivated
Read more: Debt Snowball or Debt Avalanche: Which Method Is Right for You?
#6: Learn more about money management
Whether understanding financial terms or learning how to optimize your retirement savings for taxes, you’ll feel empowered as you learn about managing your money.
Plus, it’s easier than ever with countless blogs, podcasts, YouTube videos, and other media related to personal finance.
Just remember to check the credentials of anyone giving advice or recommending a specific product.
#7: Save for retirement
What’s more empowering than feeling confident on your first day of retirement? By starting to save now, you’ll turn that vision into reality no matter how far or close you are to retiring.
In addition to contributing to your retirement savings, get smart about maximizing your balances and minimizing taxes. Take advantage of any employer contributions and research tax-advantaged accounts for which you may qualify.
#8: Work on your money mindset
No matter how much you save for your various goals, you won’t feel empowered if you don’t develop a positive attitude toward money.
Allow yourself to celebrate small milestones as you work towards different financial goals. It doesn’t have to be expensive or over-the-top, but it helps you appreciate your progress.
#9: Reassess your plan each year
Set a calendar reminder to review your financial plan at least once a year. Evaluate what worked and what didn’t while also making adjustments based on any recent or upcoming life changes.
For instance, having a child, upgrading your house, getting married or divorced—all of these personal events also impact your financial goals.
By regularly preparing and adjusting your finances, you’ll feel proactive instead of reactive. And that can help you achieve financial empowerment.
Choose your own path to empowerment
As you make financial decisions to feel more empowered, find a balance between learning from professionals and making your own priorities in life.
Creating and executing a sound financial plan will boost your confidence and help you feel more secure as you move forward in your journey.
All personal loans made by WebBank.
How to Appeal a MetLife Long-Term Disability Denial
Metropolitan Life Insurance Company—more commonly known as MetLife—is one of the world’s largest financial services companies. While MetLife is typically associated with life insurance and financial services, the company has a robust disability insurance business as well.
If you’ve recently had a long-term disability claim denied by MetLife, we understand how frustrated you might feel. Before you give up and accept MetLife’s decision, you should consult with a disability insurance lawyer at Bryant Legal Group. We have extensive experience with MetLife disability insurance appeals and can help you understand your legal options. Keep reading to learn essential steps you should take after a disability insurance denial.
MetLife Has a Track Record of Denying Valid Claims
While many of us associate MetLife with friendly images of blimps at sporting events and advertising with cartoon characters, it is a hard-nosed, savvy company. It has sometimes run afoul of state insurance regulators.
MetLife has a history of mishandling claims and even losing them. In January of 2019, New York regulators fined MetLife $19.75 million for mishandling and misplacing thousands of its clients’ pension claims. It had to pay hundreds of millions to clients whose claims were lost, delayed, or otherwise mishandled.
For large companies like MetLife, their primary goal is profit. They process thousands of claims and cutting corners is more common than any of us want to admit. However, there are ways you can protect yourself and improve your likelihood of getting the disability benefits you deserve.
RELATED ARTICLE: When Should I Speak With a Disability Lawyer?
Most MetLife Disability Insurance Plans Are Governed by ERISA
Unlike many other large insurance companies, MetLife currently doesn’t sell individual disability insurance policies to private individuals. Since September 2016, MetLife has only offered group disability coverage through employee benefit programs.
That means if you have disability insurance through MetLife, your plan is almost certainly governed by a federal law known as the Employee Retirement Income Security Act of 1974, or ERISA for short. You have certain rights and protections under ERISA. However, you also must follow strict guidelines for how and when you can appeal a disability denial or file a lawsuit, and what evidence you’re allowed to include.
The remainder of this blog post will primarily focus on the MetLife appeals process under ERISA.
If you did purchase an individual disability insurance policy directly from MetLife (not through an employer) before September 2016, and that policy remains in force, a different set of rules may apply to you. We will touch on this briefly toward the end of this article.

A Step-By-Step Look at the MetLife Long-Term Disability Appeals Process
You must act quickly once your claim has been denied. Under ERISA, you only have a limited time to appeal, and you want to make sure that initial appeal is as comprehensive as possible. You might only get one chance to add evidence to the record.
Read Your Denial Letter Carefully
MetLife is legally required to provide two critical pieces of information in their denial letter:
- The specific reason they denied your claim. For example, they might say you didn’t provide enough evidence, your condition isn’t covered, or they do not believe you meet the plan’s definition of disability.
- Their appeal procedures and guidelines. Each disability insurance company has its own administrative appeals process, and under ERISA you must appeal directly to MetLife before you can file a lawsuit in court. You also will have a maximum of 180 days to file an appeal. That might sound like a lot, but it isn’t.
Request a Copy of Your Claims File
MetLife may have provided this with your denial letter—but if they didn’t, request it immediately. Your claims file should include all the information that MetLife used to make their determination. This could include medical records, job descriptions, and other evidence.
By reviewing your denial letter, your claims file, and your plan documents, you can get a much better sense of whether MetLife’s denial was legitimate—and if not, the additional evidence you’ll need to provide for your appeal to be successful.
Contact a Long-Term Disability Lawyer
ERISA appeals are extremely risky to try to tackle on your own. The stakes are high and mistakes can be costly.
The denial letter might make it seem like MetLife’s appeals process is simple and straightforward. It isn’t. More likely than not, you will need to present extensive evidence and arguments in an organized way.
You do not want to mess this up, and building a successful appeal will take time even for an experienced attorney. The sooner you get a professional to review your case, the better your chances of success.
Gather the Necessary Evidence
Once your attorney reviews the denial letter, plan documents, and claims file—and determines you have a good case—they will start to help you gather the relevant evidence. This might include things like:
- Additional medical records
- Functional evaluations that measure your physical and cognitive performance
- Vocational evaluations of your realistic future employability and earning capacity
- Letters of support from doctors and medical staff
- Letters of support from colleagues, family members, and other individuals who are knowledgeable about your physical and mental capabilities, before and after you became disabled
- Photos, videos, journal entries, and other recordings of your daily experiences and circumstances
- Any other evidence your long-term disability lawyer might consider relevant to your case
Make Sure Your Evidentiary Record Is Complete
In an ERISA claim, you only have a limited amount of time to submit evidence. Once MetLife reviews your appeal and makes its final decision, you cannot submit additional information, no matter how important it is to your case. Even if MetLife denies your appeal, and you file a lawsuit, the court will only be able to review the evidence that is already in the claims file.
Unfortunately, many people make the mistake of submitting an appeal without additional evidence. Your lawyer can help you collect and submit evidence that supports your allegations and documents your disabilities.
File Your Administrative Appeal and Wait for a Response
Once you have your evidence together, your attorney will help you prepare and submit your appeal. This will include all the new evidence you’re adding to the claims file. It will also include a detailed appeal letter that outlines why, specifically, you disagree with MetLife’s determination and believe your benefits should be approved.
After you appeal, MetLife will have an initial deadline of 45 days to respond. This can be extended one time for an additional 45 days, so you could be waiting almost three months to find out if your appeal has been accepted.
Consider Legal Action If Your Appeal Is Denied
If your claim is denied, and there are no more mandatory administrative appeals you must go through, your final option is to file a lawsuit in court.
From here, your case will likely be reviewed by a judge (not a jury) and, as noted above, the judge will only be able to review the existing evidence in your claims file.
Even though no new evidence can be added, your long-term disability lawyer will still be able to represent your interests in court. They can prepare written briefs, present oral arguments, and explain and interpret evidence in the record.
What If I Have an Individual Disability Insurance Plan?
Although MetLife no longer sells individual disability insurance policies to private individuals, they still administer policies that were sold previously. If you have one of these “grandfathered” policies, it may be governed by your state’s contract laws rather than ERISA.
In general, policyholders with non-ERISA plans have more options when it comes to appeals. For example, you may not be required to complete an administrative review before filing a lawsuit, and you may be able to request a full jury trial.
Because each state has a unique set of contract laws, be sure to contact a long-term disability lawyer in your state as soon as possible to begin reviewing your legal options.
RELATED POST: Appealing Denied Private Disability Insurance Claims – Bryant Legal Group (bryantlg.com)


Bryant Legal Group: Disability Lawyers Who Can Fight for Your Rights
If MetLife recently denied your disability claim, it’s in your best interest to consult with a skilled lawyer at Bryant Legal Group. We are proud to help our clients assess their legal options, identify the correct procedures, “stack” their evidentiary record, and negotiate with the long-term disability company.
To learn more about our approach and how we might be able to help you, please contact us today to receive a free and confidential consultation. You can reach Bryant Legal Group by calling 312-561-3010 or completing this brief online form.
Taking your business to the next level
Growing your business requires strategic planning, effective
execution and a keen understanding of your market. Having sufficient funding in
place could help you on your journey.
LendingCrowd was created to fund the ambitions of businesses
across Britain. We combine cutting-edge technology with vast financial
experience across our team to provide fast and affordable business loans from
£75,000 to £500,000 that help SMEs to develop and grow.
Starting your journey
Before you begin, you should define your business goals and
be specific about what you want to achieve. Set SMART goals, making sure your aims
are Specific, Measurable, Achievable, Relevant and Time-bound.
It’s crucial to know your market and understand what your
customers – both existing and potential – need and want. Keep an eye on
industry developments and customer behaviour so you can identify market trends.
While attracting new customers can help your business to grow,
don’t lose focus on your existing client base. Go above and beyond, exceeding
your customers’ expectations, to encourage repeat business.
Developing a detailed business plan, including financial
projections and market analysis, will help when putting your growth ambitions
into action. An accountant or financial adviser could help to analyse your
plans.
Set for success
Growing a business takes time and effort. By staying
committed to your goals, you can set your business up for long-term success.
It’s also important to make sure that taking out a loan to
fund growth is the right decision for you and your business. If you
ever find that you are in financial difficulty, you should let your lender know
as soon as possible so you can work together to find the best solution.
It takes just minutes to apply for a LendingCrowd business
loan – start your
journey today.
Please note: all applications are subject to LendingCrowd’s
risk appetite and will be subject to clearance of AML and Cifas checks.
Loan scams: How to identify and avoid them?

A lack of financial preparation can make a person more vulnerable to loan fraud. Here are some common techniques for identifying loan fraud and ways to avoid it.
December Fed rate cut: Here’s what to expect
“The Federal Reserve Open Market Committee (FOMC) is widely expected to cut its benchmark short-term rate by 25 basis points,” said Sam Williamson, senior economist at First American. “Markets are pricing in a 99% chance of this cut, but slowing the pace of rate cuts is appropriate given the recent outperformance of the US economy and stalled progress on bringing down inflation.”
The Fed began aggressively raising rates in March 2022 to combat inflation, pushing borrowing costs to their highest levels in 23 years. While inflation has cooled significantly since then, the latest Consumer Price Index (CPI) for November rose 2.7% year-over-year, still above the Fed’s 2% target.
Experts said this persistent inflation, paired with the continued strength of the US economy, is forcing the Fed to adopt a more measured approach.
Greg McBride, chief financial analyst at Bankrate, believes the December cut could be the last for a while.
“The Federal Reserve is expected to cut interest rates for a third time, by one-quarter of a percentage point, bringing the total rate reduction to one full percentage point since September,” McBride said. “But this could be the last rate cut for a few months, especially with progress on the inflation front stalling out and the economy motoring along.”
International P2P Lending Volumes October 2024
The table lists the loan originations of p2p lending marketplaces for last month. Mintos* leads ahead of Peerberry* and Esketit*. The total volume for the reported companies in the table adds up to 342 million Euro. I track the development of p2p lending volumes for many markets. Since I already have most of the data on file, I can publish statistics on the monthly loan originations for selected p2p lending platforms.
This month Robocash* crossed the milestone of 1 billion EUR loan volume originated since launch.
Investors living in national markets with no or limited selection of local p2p lending services can check this list of international investing on p2p lending services. Investors can also explore how to make use of current p2p lending cashback offers available. UK investors can compare IFISA rates.


Table: P2P Lending Volumes in October 2024. Source: own research
Note that volumes have been converted from local currency to Euro for the purpose of comparison. Some figures are estimates/approximations.
Links to the platforms listed in the table: Bondora*, Crowdproperty*, Debitum Investments*, Esketit*, Estateguru*, Finansowo*, Finbee*, Folk2Folk*, Geldvoorelkaar*, Investly*, Iuvo Group*, Kuflink*, Kviku.Finance*, Lendermarket*, Loanch*, Mintos*, Nectaro*, Peerberry*, Proplend*, Robocash*, Swaper*, Ventus Energy*.
Notice to p2p lending services not listed:
For new companies a small listing fee applies. If you want to be included in this chart in future, please contact me for more information.
Notice to representatives of press/media: If you are interested in publishing a branded version of this table in your own layout/design, which will make a nice addendum to your coverage of p2p lending, please contact me.
Can orthorexia nervosa be grounds for SSDI benefits?
The quest for perfect health can sometimes lead to an unhealthy obsession with clean eating. This condition, orthorexia nervosa, can severely impact daily life and work abilities. As more people learn about this disorder, many ask: can orthorexia nervosa qualify for Social Security Disability Insurance (SSDI) benefits?
What is orthorexia nervosa?
Orthorexia nervosa is an eating disorder marked by an extreme fixation on healthy eating. Unlike other eating disorders that focus on food quantity, orthorexia centers on the perceived quality and purity of food. People with orthorexia often:
Feel intense worry about food choices
Spend too much time planning, buying and preparing meals
Cut out entire food groups they think are “unhealthy”
Experience guilt when they break their dietary rules
Avoid social situations due to their strict eating habits
Medical experts don’t currently list orthorexia in the Diagnostic and Statistical Manual of Mental Disorders (DSM-5). However, doctors increasingly recognize its harmful effects on a person’s life.
Exploring the possibilities
The Social Security Administration (SSA) doesn’t specifically name orthorexia as a qualifying condition for SSDI benefits, but this doesn’t mean people with orthorexia can’t qualify. The SSA looks at how a condition affects a person’s ability to work when it reviews disability claims.
To potentially qualify for SSDI with orthorexia, applicants must show that their condition:
Greatly limits their ability to do work-related tasks
Has lasted or will likely last for at least 12 months
Stops them from adapting to other types of work
Getting SSDI benefits for orthorexia may prove difficult, but it’s within reach. As doctors learn more about this condition, they may start to see how it can severely disable a person. If orthorexia affects your ability to work, consider talking to a disability attorney. They can guide you through the SSDI application process and help present your case effectively.The post Can orthorexia nervosa be grounds for SSDI benefits? first appeared on Disability Rights Law Center.
The Ultimate Guide To Budgeting
In today’s financial landscape, mastering the art of budgeting and money management is crucial for achieving financial stability and reaching your goals. This Ultimate Guide To Budgeting, brought to you by Badger Loans, will provide you with practical strategies and insights to take control of your finances, whether you’re just starting out or looking to improve your financial health.
Understanding the Importance of Budgeting
Budgeting is the cornerstone of sound financial management. It allows you to:
- Track your income and expenses
- Identify areas where you can save money
- Set and achieve financial goals
- Live within your means
- Prepare for unexpected expenses
By creating and sticking to a budget, you can gain a clear picture of your financial situation and make informed decisions about your money.
Creating Your Budget
Step 1: Track Your Income and Expenses
Start by recording all sources of income and every expense for at least a month. This will give you a realistic view of your financial situation.
Step 2: Categorise Your Spending
Divide your expenses into categories such as:
- Housing (rent/mortgage, utilities)
- Transportation
- Food
- Healthcare
- Debt repayments
- Entertainment
- Savings
Step 3: Analyse Your Spending Habits
Look for areas where you can cut back on unnecessary expenses.
Step 4: Set Financial Goals
Establish both short-term and long-term financial goals. These might include:
- Building an emergency fund
- Paying off debt
- Saving for a house deposit
- Planning for retirement
Step 5: Create Your Budget Plan
Allocate your income towards essential expenses, savings, and debt repayment. Use the 50/30/20 rule as a starting point:
- 50% for needs
- 30% for wants
- 20% for savings and debt repayment
Tools for Budgeting
- Spreadsheet software like Excel (Great explanation even we could use!)
- Budgeting apps (many of which offer Open Banking features)
- Traditional pen and paper
Choose a method that works best for you and stick with it.
Staying on Track with Your Budget
- Review your budget regularly
- Use automatic transfers for savings and bill payments
- Avoid impulse purchases
- Find ways to increase your income
Managing Debt
- Prioritise high-interest debt
- Consider debt consolidation options
- Negotiate with creditors for better terms
- Avoid taking on new debt while paying off existing obligations
Saving and Investing
- Build an emergency fund (aim for 3-6 months of living expenses)
- Take advantage of tax-efficient savings options like ISAs
- Consider pension contributions for long-term savings
- Explore ethical investing options aligned with your values
Thriving in Uncertain Economic Times
- Invest in recession-proof industries (healthcare, education, essential services)
- Consider starting a side business in essential services
- Buy non-perishable items in bulk to save money
- Evaluate your living situation and consider relocating if necessary
Teaching Financial Literacy to Children
- Encourage an entrepreneurial spirit
- Teach basic accounting and budgeting skills
- Highlight the value of delayed gratification
- Discuss the risks of debt
- Introduce the concepts of saving and investing
Where to Get Help
If you’re struggling with your finances:
- Seek advice from free services like Citizens Advice Bureau or The National Debt Helpline
- Consider speaking with an Independent Financial Adviser
- Contact your lenders to discuss options if you’re having trouble making payments
Conclusion
Budgeting and managing money effectively is a skill that can significantly improve your financial well-being. By following the strategies outlined in this guide, you can take control of your finances, achieve your goals, and build a more secure financial future.
Remember, Badger Loans is here to help with your financial needs. We offer unsecured loans of up to £25,000 over 1 to 60 months for UK residents aged 18 plus.
By following this guide and making informed financial decisions, you can work towards a more stable and prosperous financial future. We wish you all the best!
Apply for a Loan with Badger Loans
The post The Ultimate Guide To Budgeting appeared first on Badger Loans.







